How to Bypass SSL Pinning and Monitor iOS Network Traffic in Real-Time with Frida
How to Bypass SSL Pinning and Monitor iOS Network Traffic in Real-Time with Frida
In today's mobile security landscape, understanding how apps communicate with external servers is crucial. However, many iOS applications enforce SSL Pinning, making it difficult to intercept HTTPS traffic. In this guide, we’ll explore an advanced iOS SSL Bypass & Traffic Monitor that allows real-time network analysis.
Why SSL Pinning Bypass is Important
SSL Pinning prevents Man-in-the-Middle (MitM) attacks by enforcing strict SSL certificate validation. Bypassing SSL pinning allows security professionals to:
- Analyze API requests & responses in real-time.
- Detect sensitive data leaks in network communication.
- Test for vulnerabilities in backend APIs.
Features of the iOS SSL Bypass & Traffic Monitor
- ✅ Bypasses SSL Pinning for network traffic analysis.
- ✅ Monitors iOS Network Traffic in real-time.
- ✅ Works dynamically using Frida (no app modifications).
Installation & Setup
Step 1: Install Frida
pip install frida-toolsStep 2: Start Frida Server on iOS
./frida-server &Step 3: Verify Device Connection
frida-ps -UStep 4: Clone the SSL Bypass Script
git clone https://github.com/riyadmondol2006/ios-ssl-bypass-and-traffic-monitor.gitHow to Use the SSL Bypass & Network Monitor
Method 1: Attach to a Running App
frida -U -p <PID> -l ios_ssl_bypass_and_traffic_monitor.jsMethod 2: Launch an App with Monitoring Enabled
frida -U -f com.example.appname -l ios_ssl_bypass_and_traffic_monitor.js --no-pauseInterpreting the Output
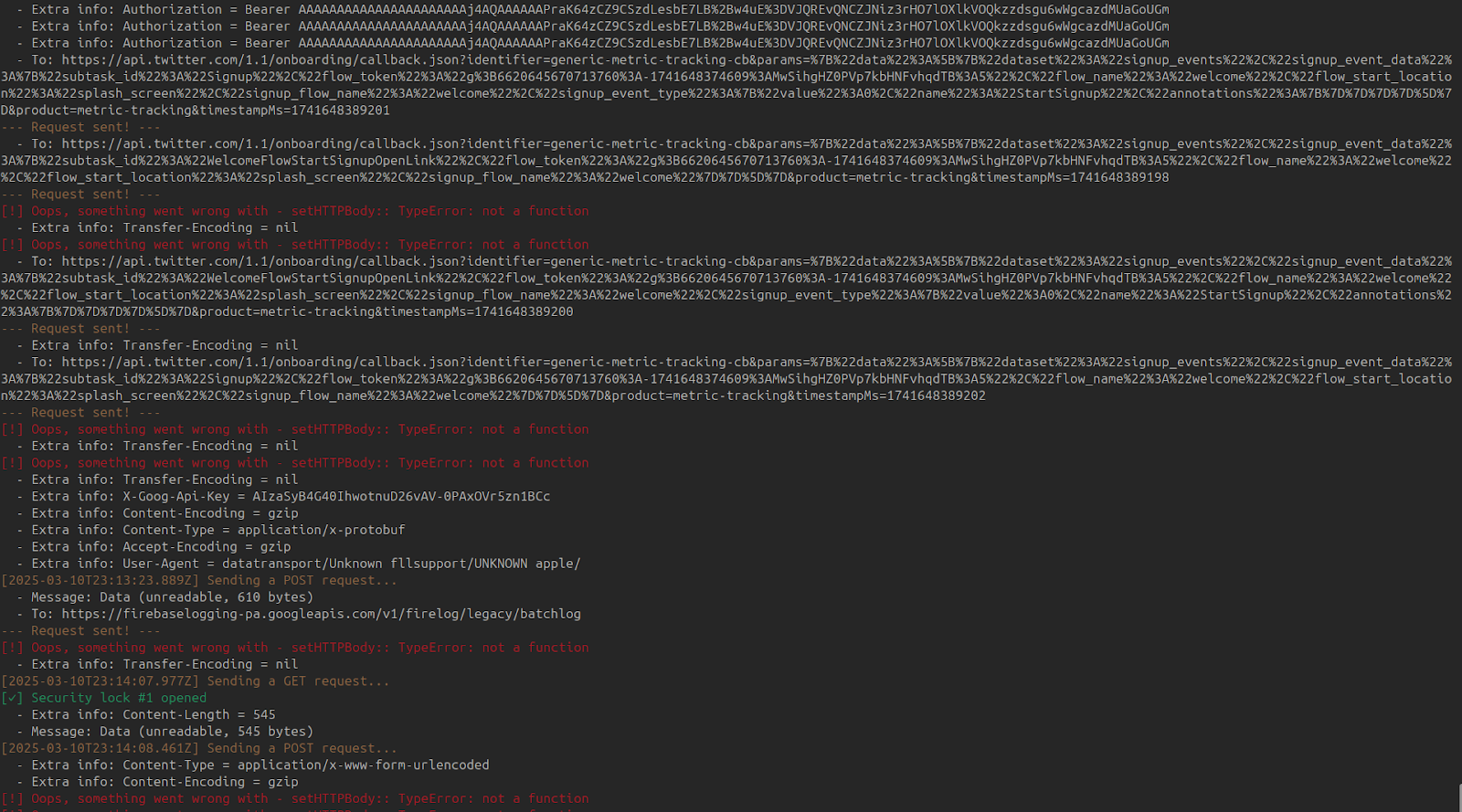
Example logs:
[2025-03-11T07:23:25.123Z] Sending a POST request...
- URL: https://api.example.com/login
- Headers: Authorization = Bearer <token>
- Body: {"username": "test", "password": "password123"}Common Issues & Troubleshooting
- 🚫 Frida Not Detecting iOS Device? Ensure Frida server is running on iOS.
- 🚫 No Network Requests Showing? The app may use a different networking method.
- 🚫 App Crashes on Attach? Some apps have Frida detection, requiring extra steps.
Conclusion
Bypassing SSL Pinning is crucial for security testing and debugging iOS apps. The iOS SSL Bypass & Traffic Monitor makes it easy to analyze app communication without modifying the app.
Resources & Further Learning
- 🔗 GitHub Repo: iOS SSL Bypass & Traffic Monitor
- 🔗 Frida Documentation: Frida Docs
- 📺 YouTube Tutorials: Reversesio
Contact Information
📩 Email: riyadmondol2006@gmail.com
💬 Telegram: @riyadmondol2006
🚀 Want more security tutorials? Follow Reversesio on YouTube!



Comments